Tours and activities are all about fun. And as a tour operator every day should be about providing the best experience possible to guests. Nothing dampens the mood quite like a cyber attack, where your client’s information, your website, and your reputation as a business can all fall victim. Cyber security and cyber hacking are both big business, with the former estimated to cost the world economy $6 TRILLION ANNUALLY by 2021(opens in a new tab).
With so many resources invested in exploiting security lapses across the internet, it’s especially important that you take all necessary precautions(opens in a new tab) to protect both your business, and your guests’ information. Your website is the gateway to your business so maintaining its security is as essential as the safety of the guests who take your tours. We’ve put together some useful tips to ensure that you and your guests are protected so that they can go through your site with confidence, and you know everyone’s data stays secure.
SSL Certification
An SSL certificate is proof that your website is using a secure, encrypted connection. This means that if a visitor’s information were to be intercepted, the hacker would be unable to understand it – thereby protecting both you, the site owner, and your website visitor. It’s easy to check whether your site has a valid SSL certificate, go to your site and check the address bar at the top (or bottom) of your browser. If your domain name is preceded by https://, then you’re using a H-T-T-P-Secure connection. If not, and your domain begins with http:// then contact your hosting provider. They should be able to upgrade your plan fairly easily.
Privacy Policy
Whether filling in forms leaving their personal details, booking a tour, or merely just by browsing your site, the modern-day surfer is aware that they’re providing you with information, and they’re more wary than ever about how you use it. In addition, a Privacy Policy is a legal requirement in countries such as Australia and within the European Union. Your Privacy Policy should clearly explain what information you are gathering from your website visitors and your justification for doing so. Also where and how you store the information you collect, and with whom you share it (where relevant). This allows people to make informed decisions, and in most cases put them at ease.
Contact Information
This is more relevant for ensuring peace of mind for your guests(opens in a new tab), with nearly half (44%) of internet users(opens in a new tab) saying that they would leave a website without interaction where there is no available method of contact other than an email address. If you have a physical address then make sure it’s easy to find, preferably in the website footer, as well as on your contact page. If not, then providing a contact number, along with meeting locations (and staff profiles) is the next best thing.
Secure Your Backend Login
One of the most common types of password hacking is known as a ‘brute force attack’. This is where a computer program attempts to gain access to your account by randomizing potential passwords – starting with the most commonly used eg. password123. One of the most obvious ways to combat this is by setting a complex, strong password. Best practice also indicates that you use different passwords for different logins and don’t store those passwords somewhere where other people could access that information whether it be online or on a sticky note on your desk.
However, due to modern processing power, this may not be enough. A lot of online companies are moving over to MFA (Multi-Factor Authentication, or 2-step authentication). This involves entering a password, followed by a secondary authentication step. This could be a code sent via email, SMS, automated voice call, or mobile application that is valid for a set period of time. It’s possible to add 2-Step Authentication on WordPress, SquareSpace, Wix, and most other CMS and website builders for extra security.
Malware Security
Even when your site has an SSL certificate and your account login secure, it’s still possible for malware to infect your site through third-party integrations. Malware is code inserted in software (or even the software itself) that is used for illicit means. This includes identity theft, stealing financial data, and infecting computer systems in order to mine cryptocurrency. To ensure your site is free from malware, only integrate third party software developed by reputable sources. Keep your plugins and third-party integrations up to date on the latest, stable versions and carry out regular malware scans. At Tourism Tiger(opens in a new tab), we use Sucuri(opens in a new tab) which carries out a full site scan as regularly as every 30 minutes, with alerts and automatic malware removal depending on your plan. Of course, software such as Sucuri is an additional investment, but the cost of being hacked could be much higher.
Create Site Back-Ups
Ensure that you’re backing up your website on a regular basis, so in the event of an attack, or if you accidentally install malicious software on your website, you’re able to roll back the clock easily with minimum damage. Your hosting provider may offer regular backups as part of your plan but if not, make an offline backup of your site at least once a week, or before and after making manual changes. At TourismTiger, all of our websites are backed up every 24 hours, so if something happens in the backend of the site it’s super easy to fix.
Beware of Phishing Scams
Don’t let yourself become the access point between cyber criminals and your business. A phishing scam(opens in a new tab) is where an individual receives a text message, email, or telephone call from someone posing as a (usual well-known) organization. In most cases, the fraudster will inform the victim that there has been fraudulent or suspicious activity on their account and ask them to sign in via an embedded link to ‘secure the account’. Of course, when the victim enters their details, the fraudster captures them and is then able to access the real account. If you do receive an unexpected email purporting to be from a company with whom you do have an account, best practice would be to navigate directly to the page in question using your browser (without clicking the link in the email) and to check for messages.
An example of a phishing attempt:
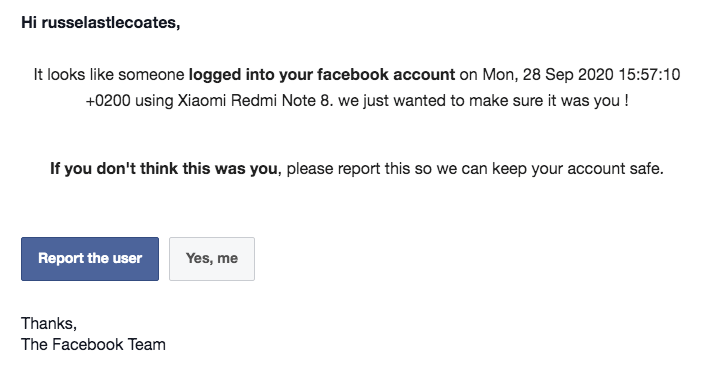
Email purporting to be from Facebook asking me to secure my account from ‘FBSupport’. But on closer inspection, the email address that sent this ‘suspicious login attempt’ is quite obviously not Facebook official :

Use a Payment Processing Gateway
This type of software allows your clients to make secure, easy payments online through your website or reservation management system. When they submit their card details, this data is sent directly to the payment gateway over a secure network. When the payment gateway software receives the payment details, it encrypts them and sends the data onto the merchant’s processor. Within seconds, the transaction is approved or rejected by the issuing bank. If it’s approved, the transaction is sent back to the payment gateway, which transmits it back to the website.
Even if you didn’t quite follow that process, it’s easy to see that an immediate, encrypted transaction is much more secure than a client filling in their card details through an online form that sits in the backend of a website. PayPal, Stripe, and Square are all well-known payment gateways, but be sure that whichever company you choose works in both the currency you bank in and that which your guests will be using.
There are many other factors that you should consider when securing your website. The ones I’ve included here will be a good starting point for your business, and will ensure a minimum level of security. If you have any other suggestions leave a comment before or get in touch with us(opens in a new tab) to learn more about the cyber security measures we put into our sites!
Find this article useful? Enter your details below to receive your FREE copy of 95 Epic Places To List Your Tours and receive regular updates from Tourism Tiger and leading industry experts.
By submitting this form, you agree to Tourism Tiger contacting you via email.